Scenario:
- You want to use a fully hosted, fast and secure recursive DNS for your network (office, home/home office, branch)
- You need to protect your internal clients and your whole network from malware activity, from phishing attempts and from botnets at the DNS level – that is – before any harm is done
GSLB.me recursive DNS provides you with:
- Redundant, highly performing recursive DNS
- Realtime protection from thousands of malicious domains used by malware, phishing attacks, botnets
- Fully visibility and statistics on your DNS queries, with details on internal clients (private IPs) trying to access malicious/dangerous domains
How to configure it:
Log on to GSLB.me using your credentials or register if you still don’t have an account
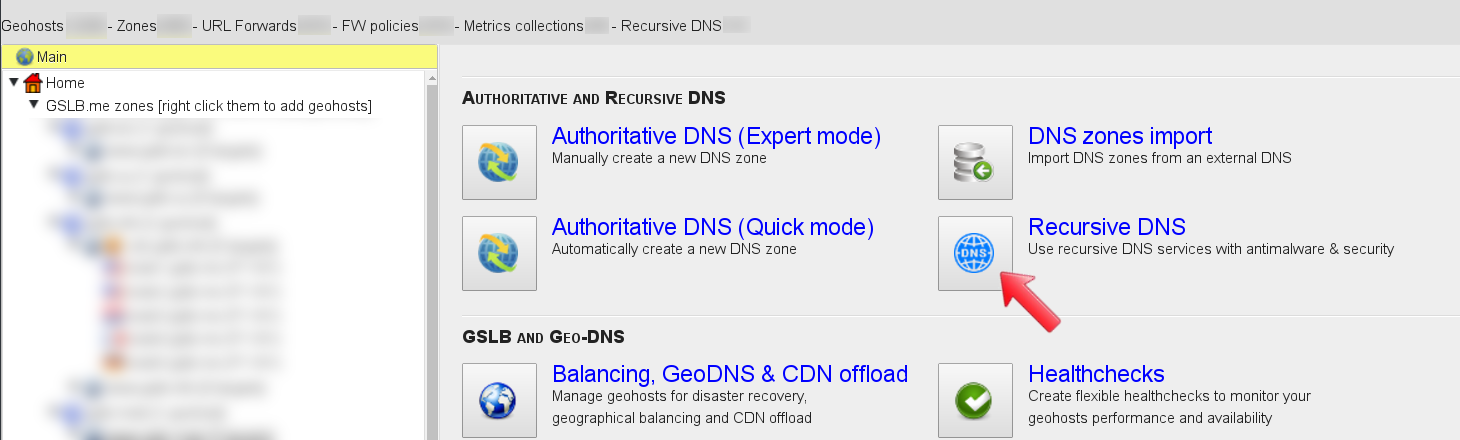
From the main dashboard click on the “Recursive DNS” icon, this will lead you to the recursive DNS configuration section
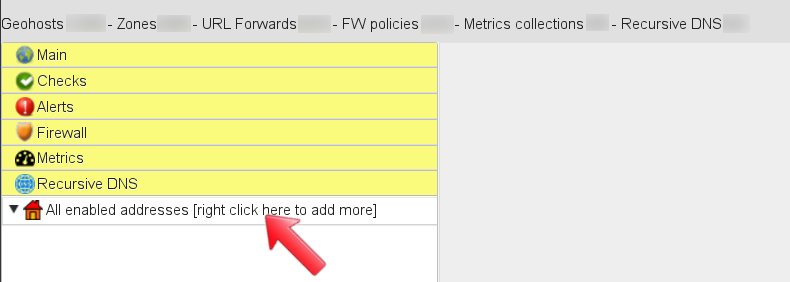
Right-click on “All enabled addresses” to define the Internet-facing (public) IP address that will use GSLB.me as its recursive DNS. It is likely that you have several clients on one or more private subnet source NAT-ted through the public IP address. In such a case GSLB.me will provide recursive DNS services and malicious domains protection to your whole network.
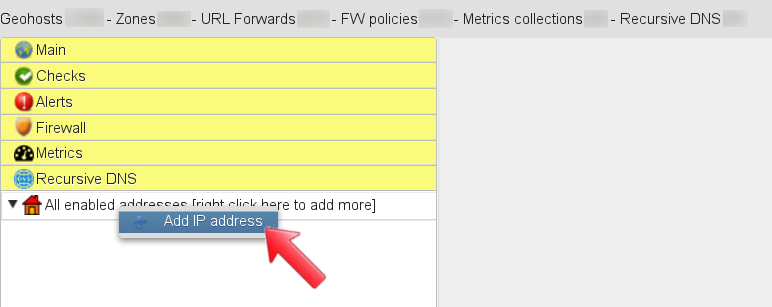
From the menu click on “Add IP address”, this will allow you to configure the Internet-facing (public) IP address that will send DNS queries to GSLB.me recursor
The Recursive DNS configuration dashboard is where you can enter your public IP address, a mnemonic description, and you can associate one or more alerts: GSLB.me will notify you in case DNS requests for malicious domains come from your public IP/internal network.
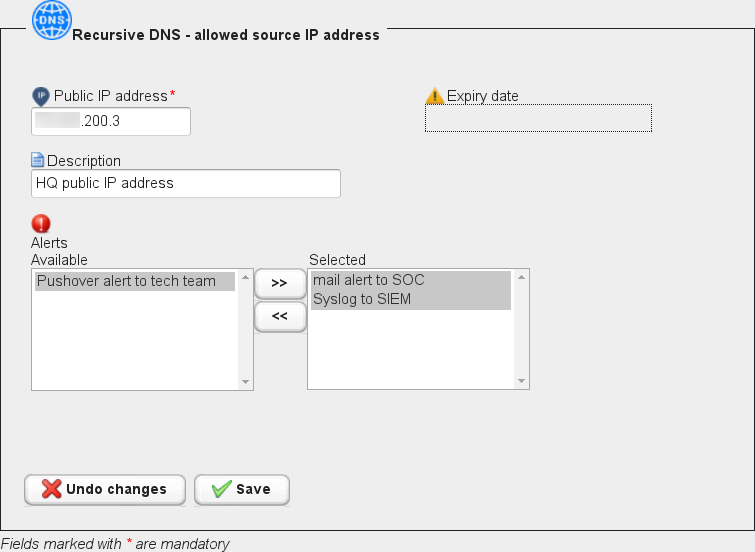
When done, click on “Save”, to save and commit your configuration.
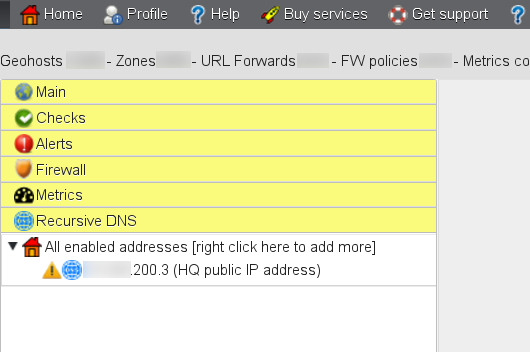
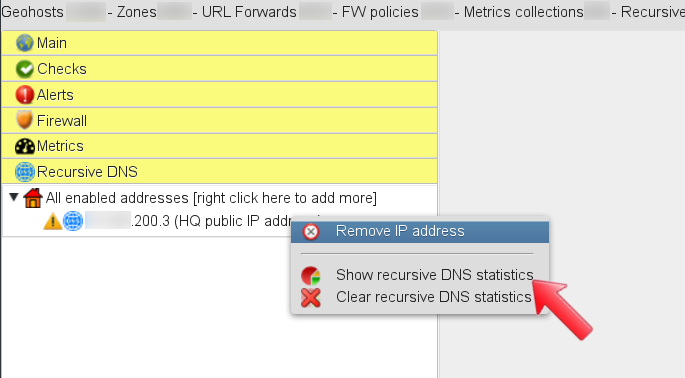
The newly configured IP address is displayed in the “Recursive DNS” section of the main menu. Right-clicking on the IP address you can access the menu where the IP can be removed, and where statistics can be accessed. Click on “Show recursive DNS statistics”: To start using GSLB.me as your recursive DNS you need to use IP addresses 108.61.210.251 and 108.61.216.224 as your DNS servers. Should you need assistance to do so, our technical support team is here to help you, drop us a line and let us know how we can assist you.
From now on, GSLB.me will handle your DNS queries, by resolving legitimate hostnames, by blocking malicious/harmful ones while alerting you if you set up at least one alert.
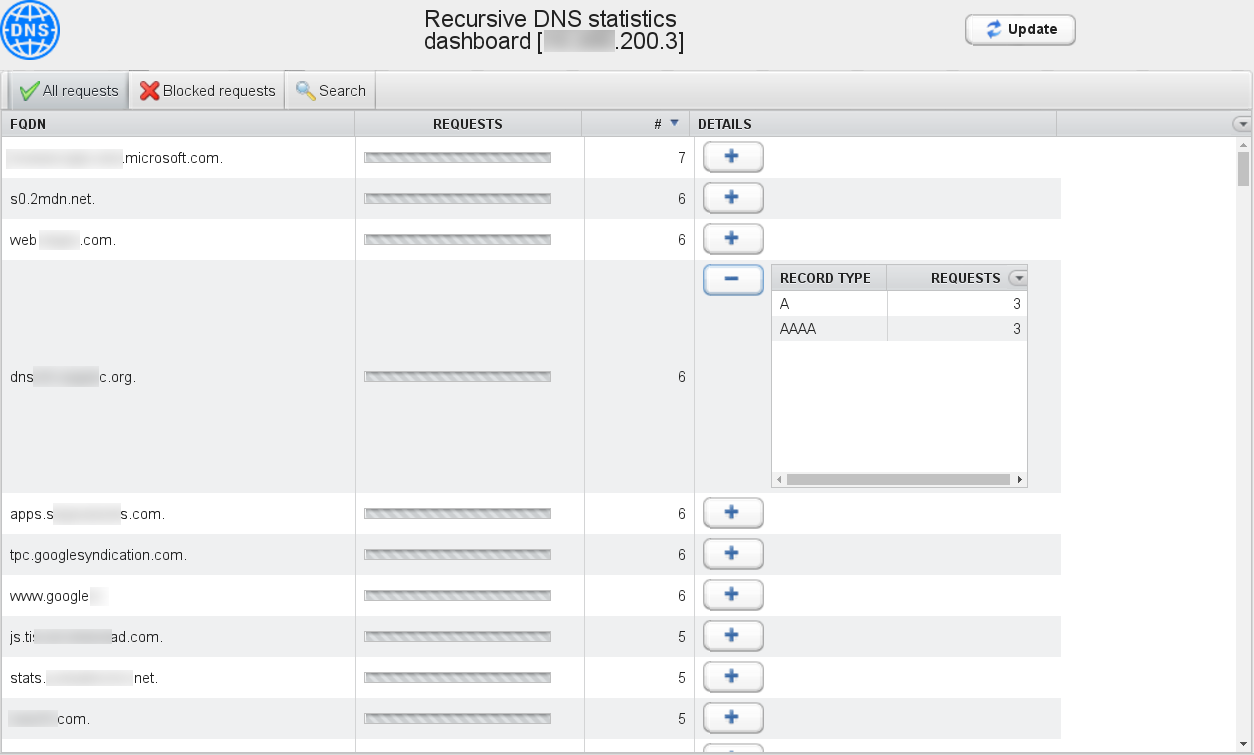
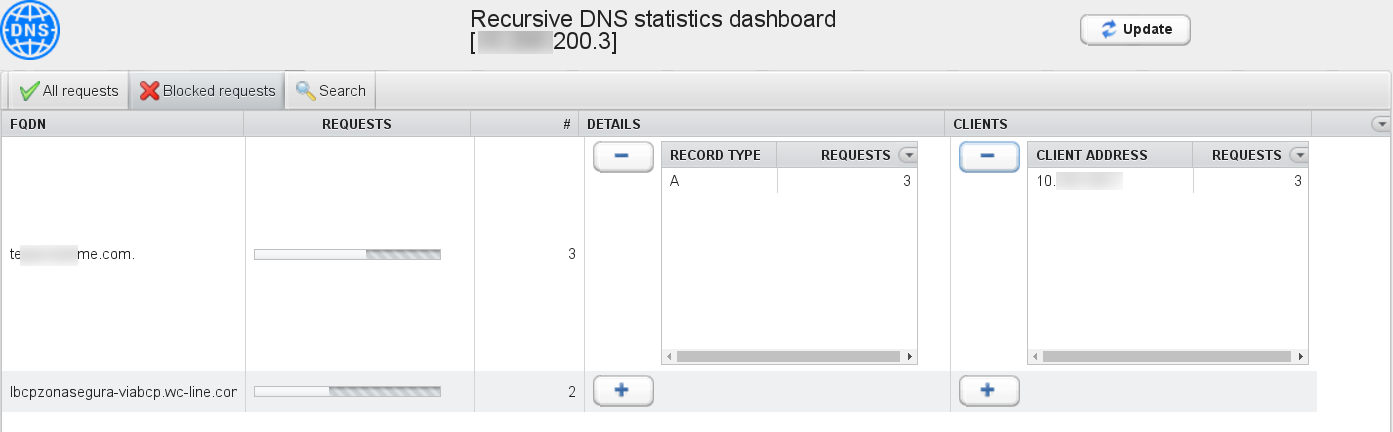
The statistics dashboard displays all DNS requests coming from your public IP address, with details on query types and number of occurrences. The “Update” button can be used to refresh the statistics table.
The “Blocked requests” tab summarizes all host names for which DNS resolution has been request to GSLB.me and that have been blocked. The “Clients” column details the private IP address of the client that tried to resolve the harmful hostname. In order for GSLB.me to correctly display the internal (private) IP addresses of your clients, you need to set up a forwarding DNS server in your network. Such a forwarding DNS will be queries by clients in your network, will add the “EDNS Client Subnet” option in outgoing queries, and eventually send all queries to GSLB.me. Please see below for configuration tips on how to setup a local resolver DNS that uses GSLB.me as your Internet DNS resolver.
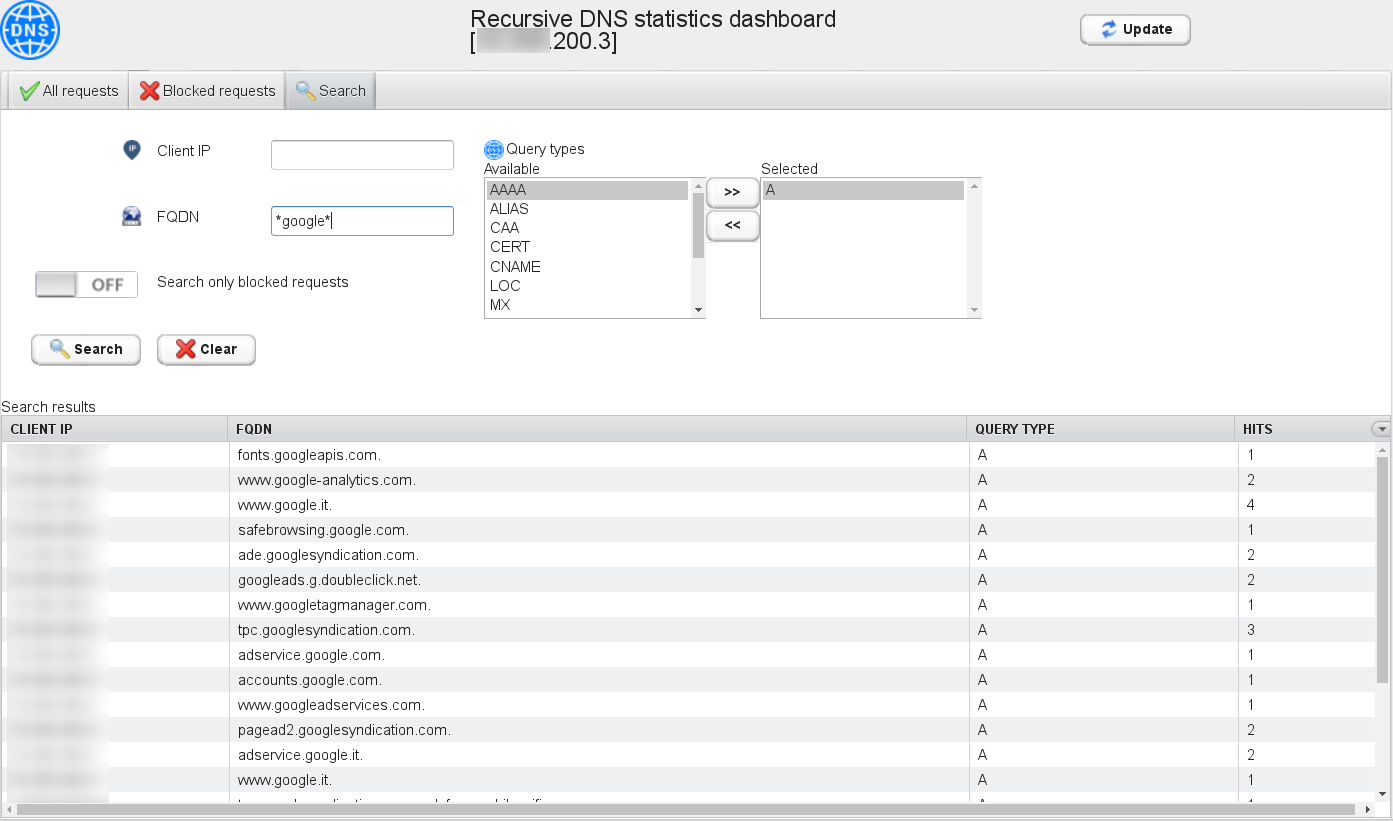
The “Search” tab allows you to look for specific hostnames and query types:
Local DNS configuration hints
In order to unleash the full power of GSLB.me recursive DNS we strongly recommend to run a resolver DNS locally on your network. This resolver DNS must then use 108.61.210.251 and 108.61.216.224 as its upper-level resolver DNS. Such a setup will ensure that all DNS queries coming originating from your network are sent to GSLB.me for screening and processing. Additionally, we also recommend you to configure your local resolver DNS so that the “EDNS Client Subnet” field is inserted in all outgoing DNS queries.
Here’s some tips on how to achieve this:
dnsmasq
add the following lines to your dnsmasq.conf configuration file:
# Don't rely on /etc/resolv.conf no-resolv # Use GSLB.me resolver IP addresses for DNS queries resolution server=108.61.210.251 server=108.61.216.224 # Inserts the EDNS Client Subnet field in outgoing queries add-subnet=32
Drop us a line!
If you need assistance setting up your favourite local DNS resolver, let us know and we will help you.
